
1. Access Management
1.1) 종류
- Serial Console Port
- Telnet
- SSH
- Web Management GUI
- SNMP-based management apllications
- RUCKUS SmartZone and RUCKUS Cloud
- RUCKUS Unleashed
1.2) Serial Console Port
1.2.1) USB Type-C & RJ-45
- ICX7150 / ICX7550 / ICX7660 / ICX7850
1.2.2) Mini-USB & RJ-45
- ICX7450 / ICX7750
1.3) Remote Access Options
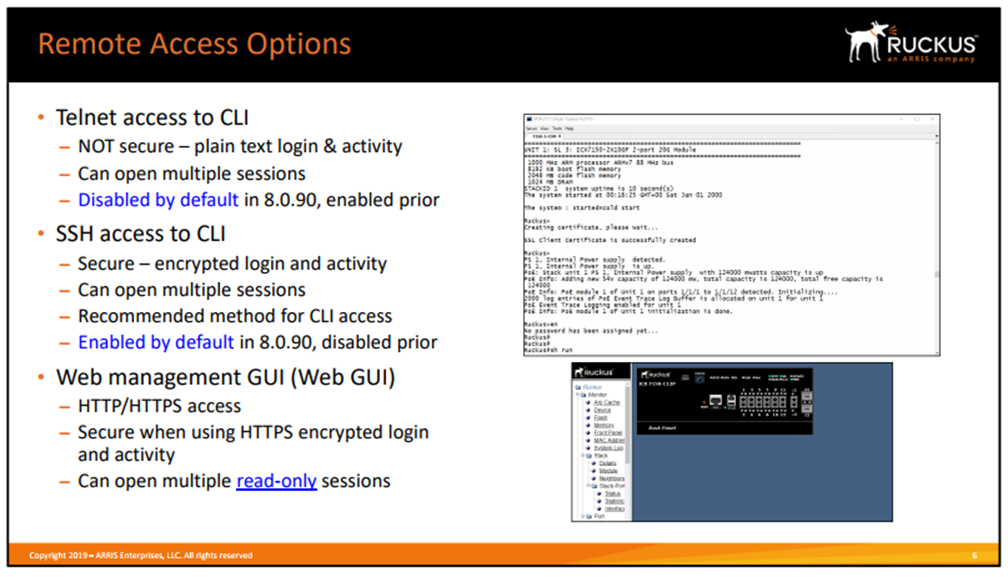
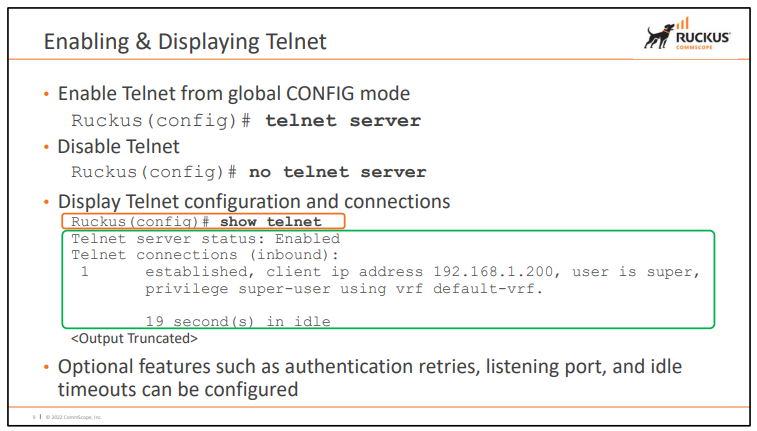
1.3.1) Telnet
- 08.0.90 부터는 기본 값이 Disable / 이전 버전은 Enable
Pod4-SW3#show telnet
Telnet server status: Enabled
Telnet connections (inbound):
1 established, client ip address 192.168.6.106, user is super, privilege super-user
using vrf default-vrf.
2 second(s) in idle
2 closed
3 closed
4 closed
5 closed
6 closed
7 closed
8 closed
9 closed
10 closed
Telnet connections (outbound):
11 closed
12 closed
13 closed
14 closed
15 closed
telnet@Pod4-SW3#show telnet config
Telnet server : Enabled
Idle timeout (minutes) : 4
Login timeout (minutes) : 2
Login retries : 4
Authentication : Disabled
suppress-reject-message : Disabled
Telnet IPv4 clients : All
Telnet IPv6 clients : All
Telnet IPv4 access-group :
Telnet IPv6 access-group :
telnet@Pod4-SW3#
1.3.2) SSH
- 08.0.90 부터는 기본 값이 Enable / 이전 버전은 Disable
Pod4-SW3#show ip ssh
Connection Version Encryption Username HMAC Server Hostkey IP Address
Inbound:
1 SSH-2 aes256-ctr super hmac-sha1 ssh-rsa 192.168.6.106
Outbound:
SSH-v2.0 enabled; hostkey: RSA(2048)
SSH@Pod4-SW3#show ip ssh sessions
SSH server status: Enabled
SSH copy-received-cos status: Disabled
SSH connections:
SSH connections (inbound):
1 established, client ip address 192.168.6.106, server hostkey RSA, user is super, privilege super-user
using vrf default-vrf.
you are connecting to this session
2 closed
3 closed
4 closed
5 closed
6 closed
7 closed
8 closed
9 closed
10 closed
SSH connection (outbound):
11 closed
12 closed
13 closed
14 closed
15 closed
16 closed
17 closed
18 closed
19 closed
20 closed
21 closed
22 closed
23 closed
24 closed
25 closed
26 closed
27 closed
SSH@Pod4-SW3#
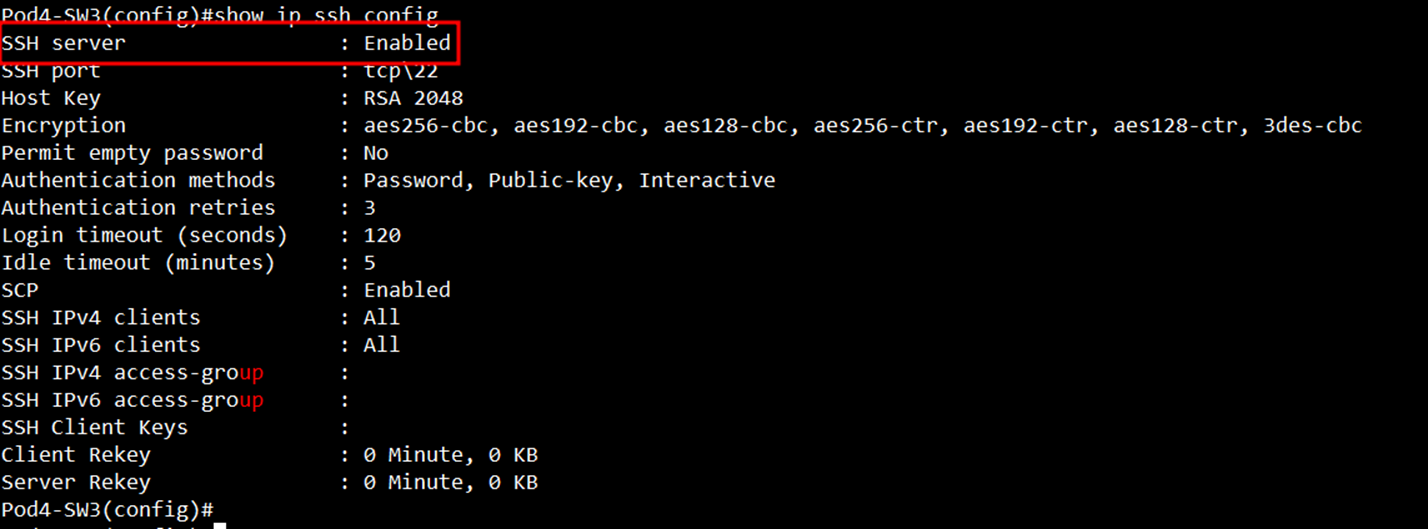
Pod4-SW3#show ip ssh config
SSH server : Enabled
SSH port : tcp\22
Host Key : RSA 2048
Encryption : aes256-cbc, aes192-cbc, aes128-cbc, aes256-ctr, aes192-ctr, aes128-ctr, 3des-cbc
Permit empty password : No
Authentication methods : Password, Public-key, Interactive
Authentication retries : 3
Login timeout (seconds) : 120
Idle timeout (minutes) : 5
SCP : Enabled
SSH IPv4 clients : All
SSH IPv6 clients : All
SSH IPv4 access-group :
SSH IPv6 access-group :
SSH Client Keys :
Client Rekey : 0 Minute, 0 KB
Server Rekey : 0 Minute, 0 KB
Pod4-SW3#
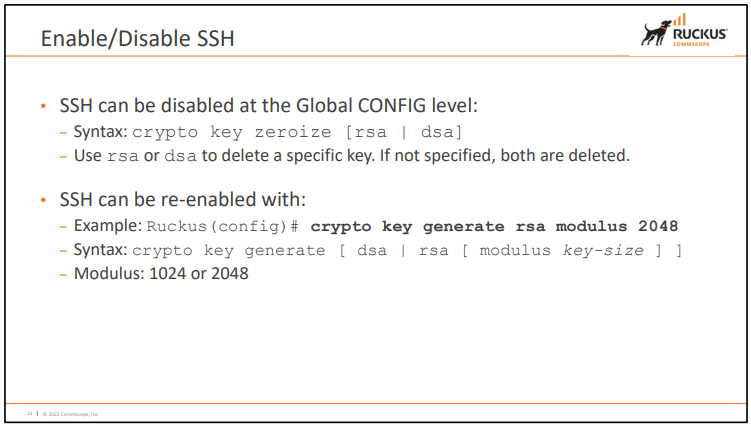
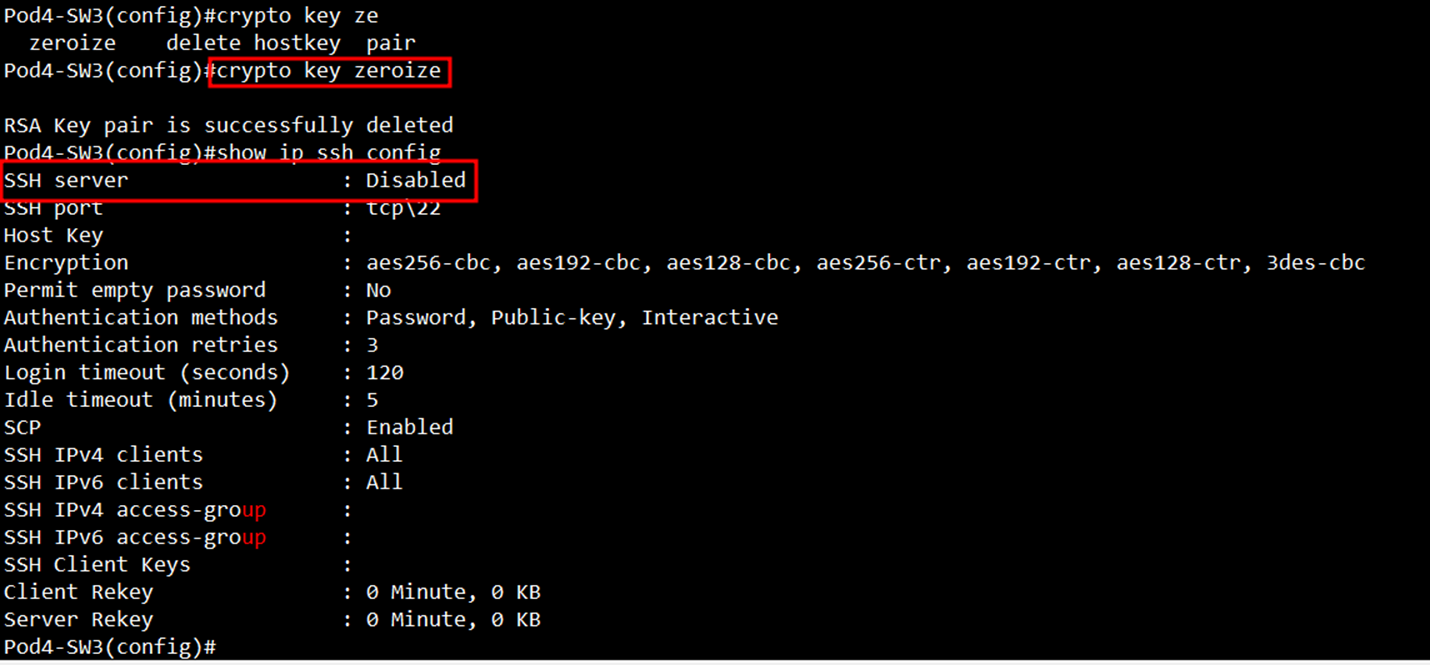
- SSH Server의 기능을 켜고 끄는 명령어 X
- 가지고 있는 RSA 키값을 지우면 SSH Server가 Disabled로 변함
Pod4-SW3(config)#crypto key generate
dsa generate dsa key pair
ec generate elliptical key pair
rsa generate rsa key pair
<cr>
Pod4-SW3(config)#crypto key generate rsa
label input rsa label
modulus generate rsa key size (1024/2048) in non-FIPS mode or 2048 in
FIPS/CC mode
<cr>
Pod4-SW3(config)#crypto key generate rsa mo
modulus generate rsa key size (1024/2048) in non-FIPS mode or 2048 in
FIPS/CC mode
<cr>
Pod4-SW3(config)#crypto key generate rsa modulus
DECIMAL enter (1024/2048) in non-FIPS mode or 2048 in FIPS/CC mode
Pod4-SW3(config)#crypto key generate rsa modulus 2048
Creating RSA key pair, please wait...
Pod4-SW3(config)#
1.3.3) Web Management GUI
- HTTP / HTTPS 모두 지원
- 다수의 Read-Only Session Open 가능
SSH@Pod4-SW3#show running-config | include aaa
aaa authentication web-server default local
aaa authentication login default local
enable aaa console
SSH@Pod4-SW3#
- HTTP 접속
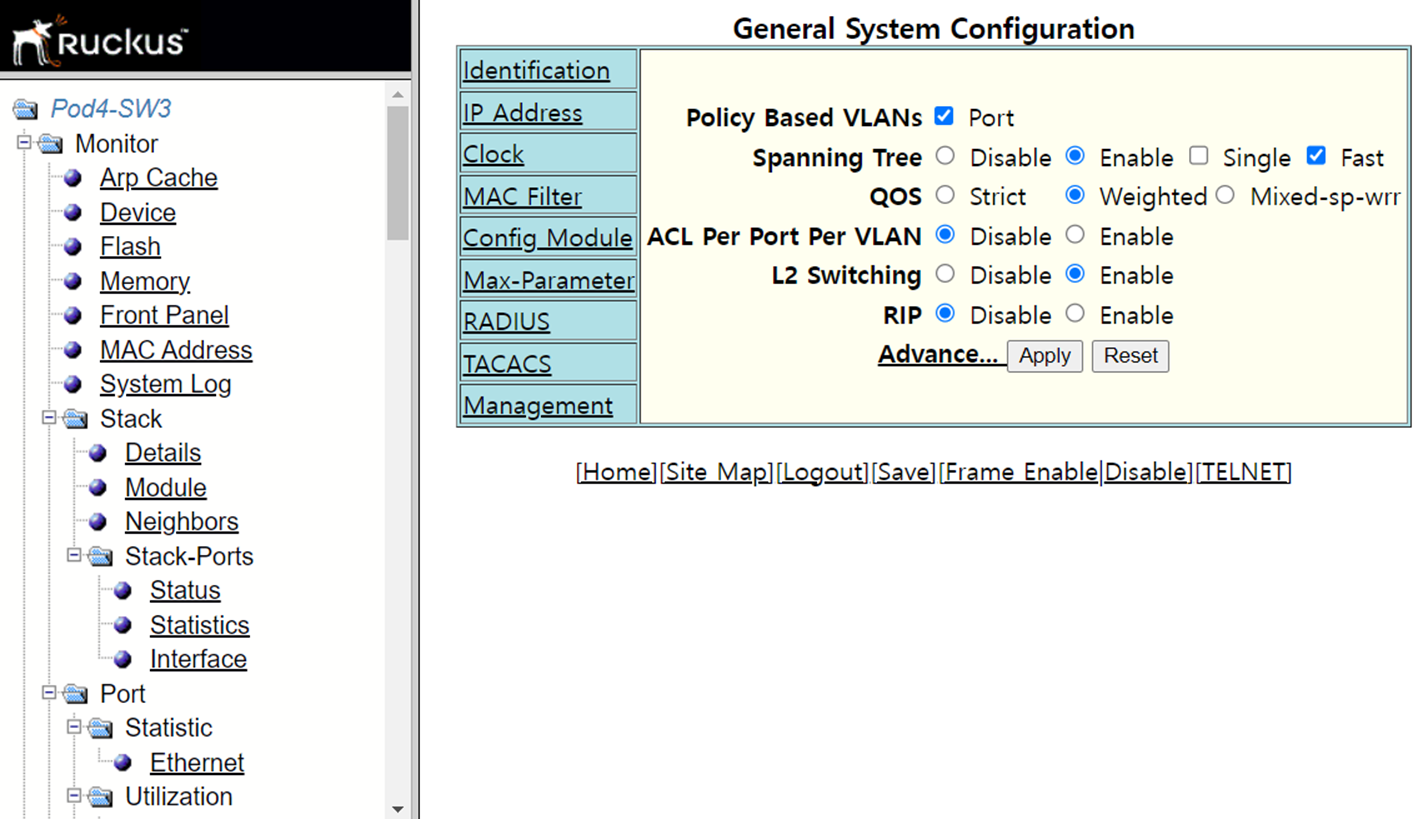
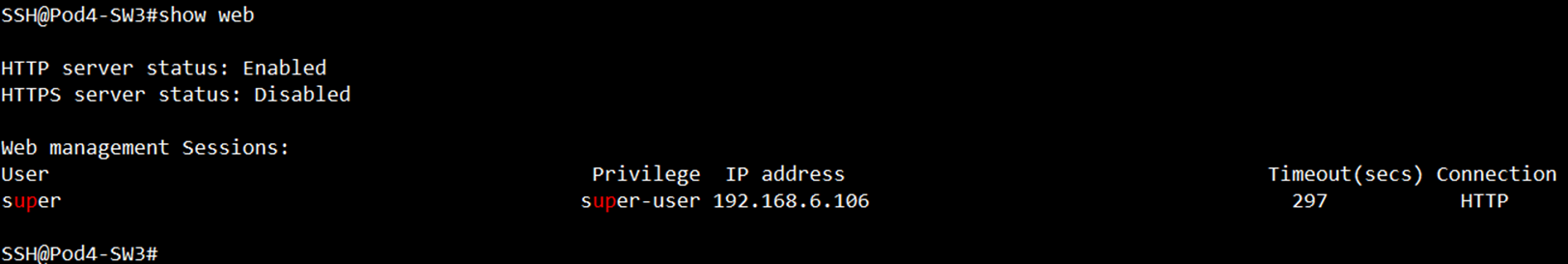
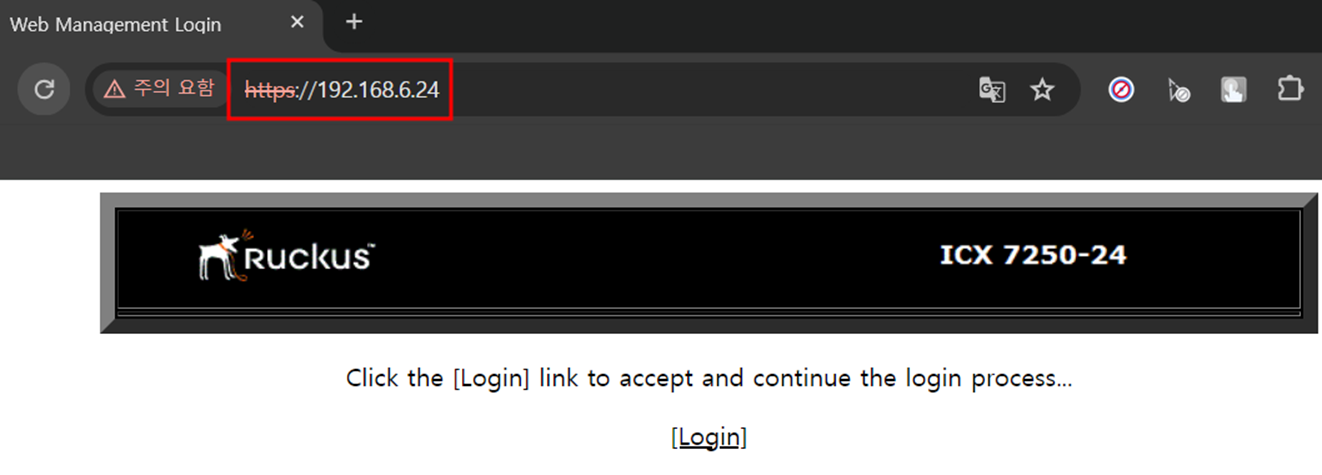
- HTTPS 접속
SSH@Pod4-SW3(config)#no web-management
allow-no-password Allow web server to have no password
connection-receive-timeout Web connection receive timeout
enable Enable web management
frame Allow to disable or enable a frame
front-panel Enable front panel
hp-top-tools Enable the support of HP TOP Tools
http Enable/Disable http access
https Enable/Disable HTTPS access
list-menu Show web menu as a list
page-menu Enable page menu
page-size Maximum number of entries in a page
refresh Page refresh (polling time) in seconds
session-timeout Web session timeout
tcp-port http port (default port 80)
<cr>
SSH@Pod4-SW3(config)#no web-management http
SSH@Pod4-SW3(config)#web-ma
web-management Web management options
SSH@Pod4-SW3(config)#web-management https
SSH@Pod4-SW3(config)#
SSH@Pod4-SW3(config)#crypto-ssl certificate generate
SSH@Pod4-SW3(config)#
Creating certificate, please wait...
SSH@Pod4-SW3(config)#exit
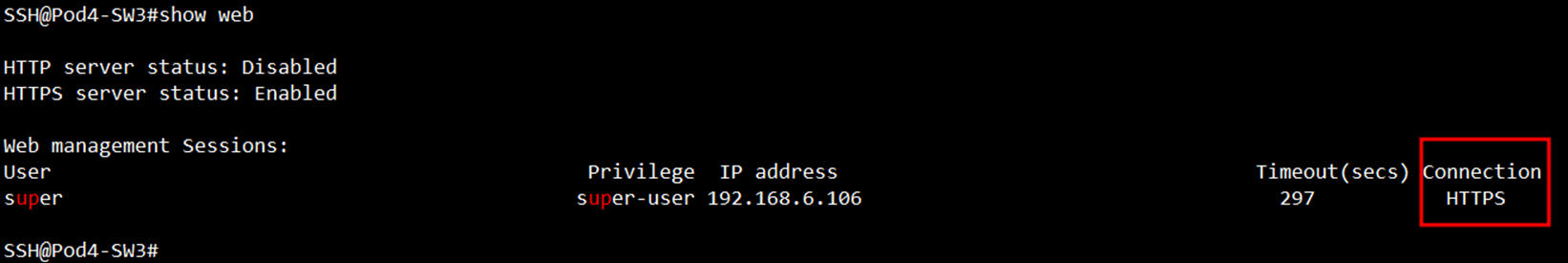
SSH@Pod4-SW3#show web
HTTP server status: Disabled
HTTPS server status: Enabled
No web connection.
SSH@Pod4-SW3#
ssl-certificate creation is successful
SSH@Pod4-SW3#
1.4) Management
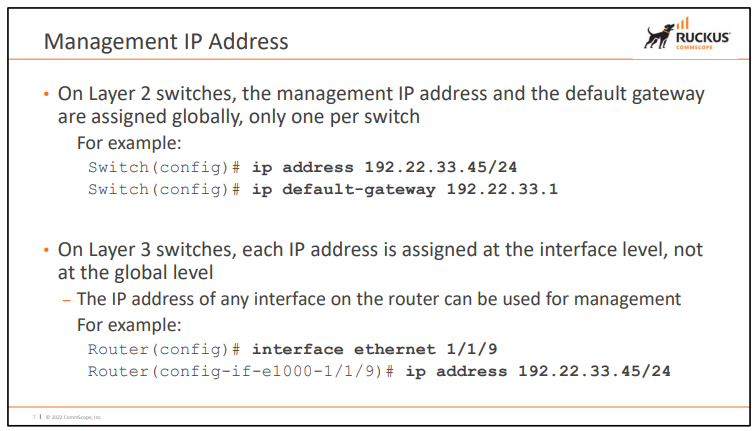
1.4.1) IP Address
- L2 = Switch 별 한 개의 MGMT IP와 Default Gateway만 가능
- L3 = Switch의 Port 별로 MGMT IP
1.4.2) Ports
- Out Of Band(OOB) 가 존재하여 관리 가능
- 08.0.50 부터 OOB Port에 MGMT VLAN이 설정되면 untagged port로 동작
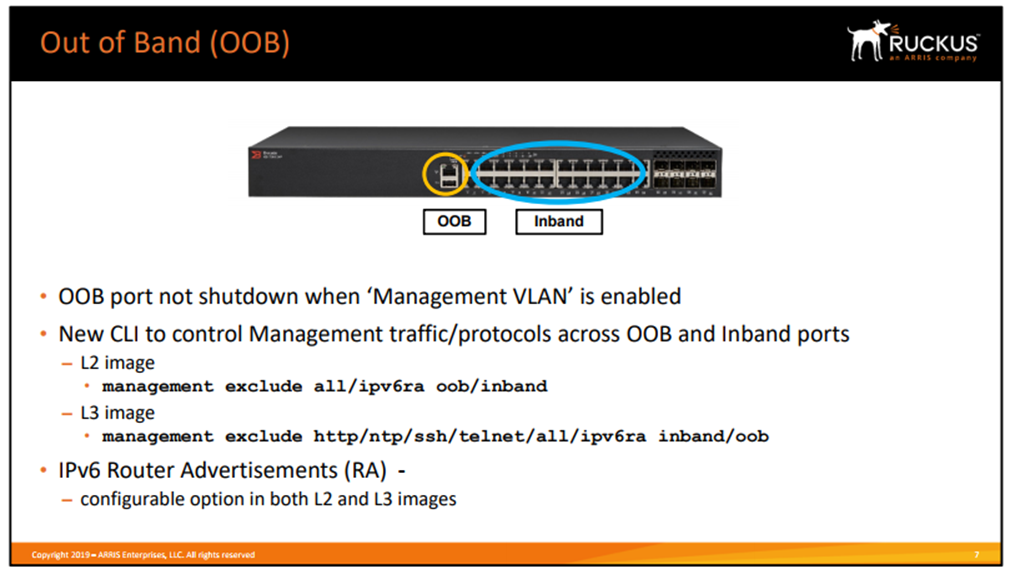
- OOB(L2 Image)
- MGMT Port(Int management 1) 이용
- MGMT Port 또는 전역 구성모드에서 관리 IP 설정 (이 둘이 동일함)
- MGMT Port의 VLAN는 기본적으로 None 값이며 특정 VLAN을 MGMT VLAN으로 규정
- 해당 VLAN에 포함되는데 권장하지는 않음
- Inband를 통한 접속에 영향을 받기 때문
- OOB MGMT Port로의 HTTP / SSH / TELNET 연결 차단 가능
- 명령어 = Management exclude all oob
- OOB(L3 Image)
- MGMT Port(Int management 1) 이용
- 관리 IP는 MGMT Port에 설정된 IP를 사용함
- MGMT Port의 VLAN은 규정할 수 없다. (MGMT VLAN 지원 안함)
- MGMT Port VRF는 기본적으로 default vrf에 포함된다.
- Vrf를 생성하고 이를 MGMT vrf로 정의한다.
- Int managament 1 을 해당 vrf에 포함한다. (VRF 지원 장비에서 구성)
- Inband와 Outband 모두 default vrf에 포함되기 때문에 MGMT vrf를 따로 구성해야한다.
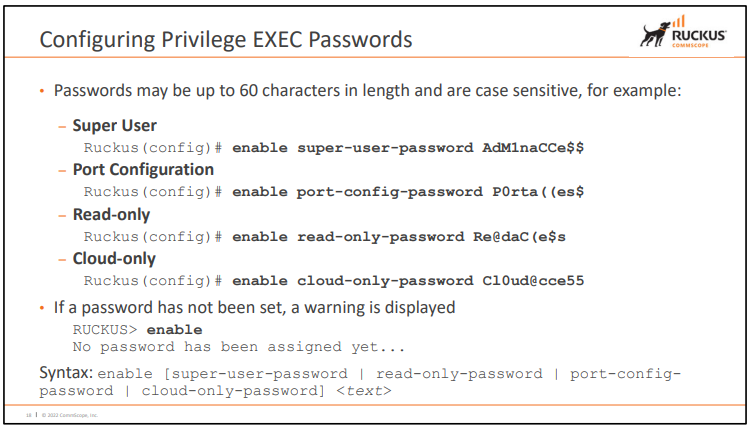
2. Privilege EXEC Passwords
2.1) 종류
- Cisco와 다르게 4가지의 레벨이 존재함
2.1.1) Super User
- Switch에 완전한 RW / RO 접근 가능 (Administrator)
- 이 Level만 Password Configuration이 가능
2.1.2) Port Configuration
- Interface Configuration은 가능하지만, Global Parameter Configuration은 불가
2.1.3) Read-Only
- Privilege EXEC Mode 접근은 가능하나, Read-Only
2.1.4) Cloud User
- show command 사용 가능 / Cloud Management 시 사용

Pod4-SW3(config)#enable
aaa Perform AAA on console
cloud-only-password cloud-only level password
egress-acl-on-cpu-traffic Enable Egress ACLs on CPU Traffic
password-display Password display control
password-min-length Minimum size of enable, local and line password strings
port-config-password Port level configuration password
read-only-password Read-only level password
skip-page-display Allow continuous display without page mode
snmp SNMP access mode
strict-password-enforcement Enforce th password security to strict level
super-user-password Super-user level password
telnet Telnet access control
user
<cr>
Pod4-SW3(config)#enable super-user-password Ruckus123
Pod4-SW3(config)#exit
Pod4-SW3#exit
Pod4-SW3>exit
Press Enter key to login
User Access Verification
Please Enter Login Name: super
Please Enter Password:
User login successful.
Pod4-SW3>en
Password:
Pod4-SW3#
'IT > ㄴ Ruckus' 카테고리의 다른 글
| [RCNI] ICX Switch SNMP 기초 [ICX150 Student Guide] (1) | 2023.12.11 |
|---|---|
| [RCNI] ICX Switch Password 및 공장초기화 [ICX150 Student Guide] (0) | 2023.12.03 |
| [RCNI] Ruckus Software Image Files [ICX150 Student Guide] (2) | 2023.12.02 |
| [RCNI] Ruckus Switch 정보 확인 [ICX150 Student Guide] (0) | 2023.12.02 |
| [RCNI] Ruckus Technologies 톺아보기 [ICX150 Student Guide] (0) | 2023.12.02 |